Torrent details for "PentesterAcademy | Cloud Security: AWS Bootcamp [2021] [FCO]" Log in to bookmark
Controls:
Language:
 English
EnglishTotal Size:
3.81 GB
Info Hash:
10a76ed75685b0ad4ca682f66f384406413dedb1
Added By:
Added:
09-10-2021 16:43
Views:
837
Health:

Seeds:
1
Leechers:
1
Completed:
624
Forum for discussion >>> https://1hack.us/
Author: Jeswin Mathai
Language: English
Released: 13 June 2021
Duration: 19h 37m 55s
Course Source: https://bootcamps.pentesteracademy.com/course/cloud-security-aws-jun-21
Description
Most AWS deployments are breached by a common set of vulnerabilities which attackers repeatedly use.
In 5 weeks, this bootcamp teaches you to identify, exploit and secure vulnerabilities in the 5 most commonly used AWS components, so you can be a job-ready Cloud Security practitioner.
What You'll Learn
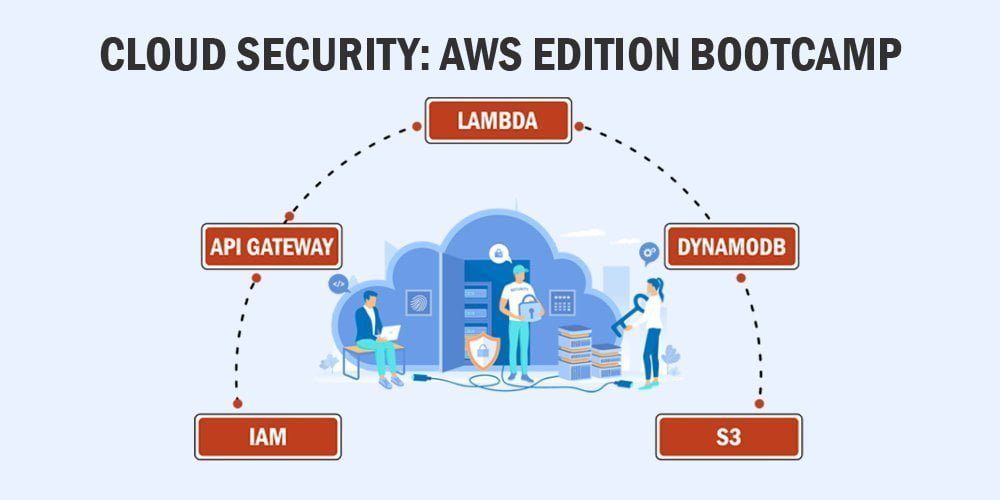
The syllabus of this bootcamp focuses on the teaching you the fundamentals and exploits for the 5 most commonly used components in AWS deployments:
1. Identity and Access Management (IAM)
2. API Gateway
3. Lambda
4. Cloud Databases
5. Simple Storage Service (Amazon S3)
To further consolidate your skills, you will be prepared to take our exam and earn the Pentester Academy Cloud Security Professional (PACSP) certification.
Build Your Cybersecurity Credentials
- Become a Pentester Academy Cloud Security Professional (PACSP)
The PACSP is proof that you’ve mastered the basics of the five most commonly used components in an AWS cloud deployment. The exam prepares you for real-world scenarios in pentesting production cloud deployments in AWS – a useful addition to the arsenal of any professional pentester.
- Bootcamp Completion Certificate
Attendees will also get a course completion certificate after attending all 5 live sessions.
Prerequisites
1. A basic knowledge of computers and networking
2. Familiarity with the Linux operating system
3. An AWS Account
About Instructor
Jeswin Mathai
He has published his work at DEFCON China, RootCon, Blackhat Arsenal, and Demo labs (DEFCON). He has also been a co-trainer in classroom trainings conducted at HITB, RootCon, OWASP NZ Day. He has a Bachelor degree from IIIT Bhubaneswar. He was the team lead at InfoSec Society IIIT Bhubaneswar in association with CDAC and ISEA, which performed security auditing of government portals, conducted awareness workshops for government institutions. His area of interest includes Malware Analysis and Reverse Engineering, Cryptography, WiFi security, and Web Application Security.











































